Introduction
Video conferences used to be a luxury reserved for corporate boardrooms, but nowadays, they’ve become an essential part of everyday work for many people. In particular, COVID-19 has driven a rapid shift to remote work, and video conferencing is now mainstream. Enterprises of all sizes rely on video conferencing to streamline workflows, collaborate effectively, and connect with clients and colleagues across the globe.
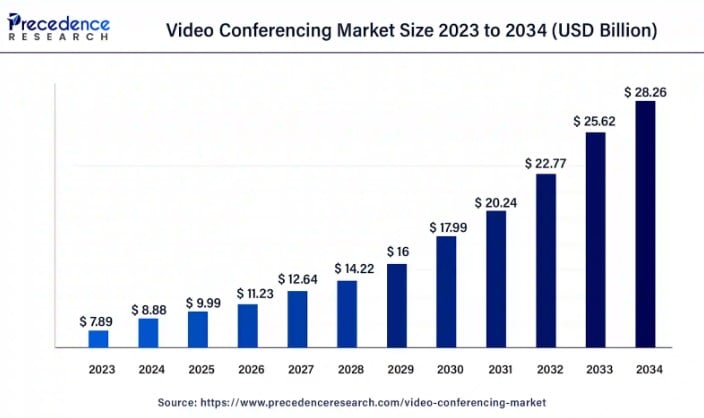
A direct result is that businesses are investing heavily in robust and secure video conferencing platforms to facilitate virtual meetings and maintain productivity. Accordingly, the demand for these platforms is growing exponentially. Studies show that the global video conferencing market is expected to grow by 14% each year from 2024 to 2034 and will reach a staggering $28.26 billion by 2034.
As video conferencing becomes more widespread, the need for stronger security measures grows. With sensitive data being shared online, keeping information safe has never been more important. Let’s explore how encryption plays a vital role in secure video conferencing platforms.
The Need for Secure Video Conferencing
For businesses handling sensitive information, security and privacy are their bread and butter. When we use video conferencing tools for personal reasons like communicating with friends, we may be less concerned about security. However, businesses prioritise protecting confidential information. Sensitive data such as future projects, demo videos, and client information need to be stored securely.
Since enterprises mostly use video conferencing, they are a prime target for cyber threats. McAfee, a renowned computer security company, reports that almost 1% of the world’s GDP (gross domestic product) is lost to cybercrime. For example, users now enjoy the ease of use that comes with many video conferencing platforms being connected to social media services like Facebook for quick account setup. However, this integration can introduce risks, such as privacy breaches, unauthorised access to video calls, and the unintended sharing of sensitive data. Security lapses like this can have severe consequences.
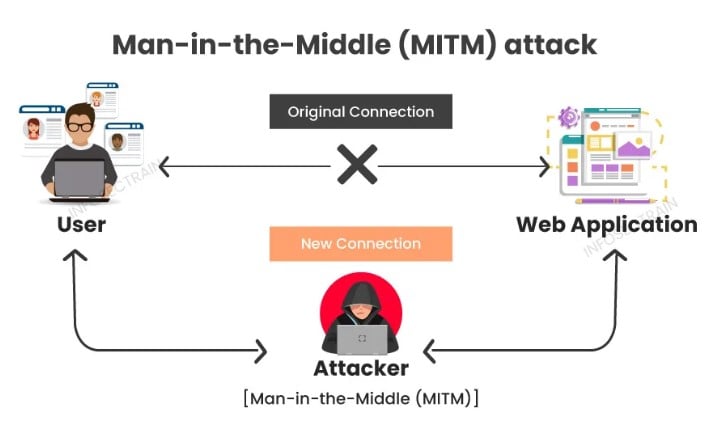
This is just one example. Here are some common security threats in video conferencing:
-
Eavesdropping: Unauthorised parties listen in during confidential meetings.
-
Man-in-the-middle attacks: Hackers intercepting communication between participants.
-
Phishing schemes: Users being tricked into sharing sensitive information through deceptive links.
-
Malware attacks: Malicious software targeting vulnerabilities in the conferencing platform.
-
Weak encryption protocols: Insufficient encryption can lead to unauthorised access to data and conversations.
There is a potential risk of confidential information being compromised and a strong need for advanced security protocols in video conferencing tools. We live in a digital era, where virtual communication is everywhere, and we need strong protections to keep our data safe from breaches and cyberattacks.
Understanding Encryption in Video Conferencing
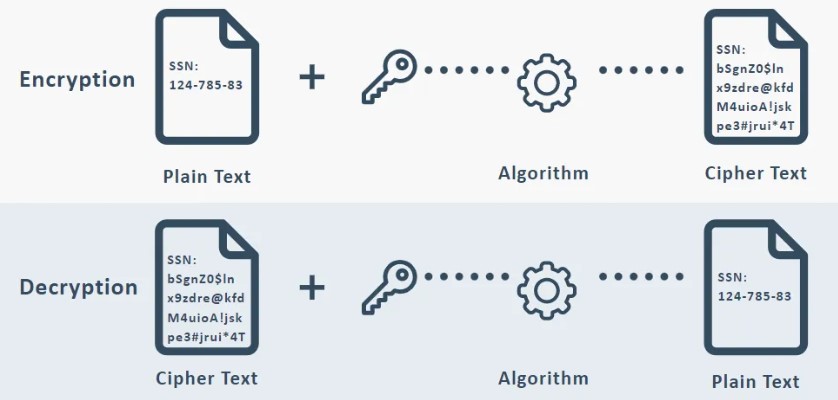
Encryption is a security measure that can be used to protect data by converting it into a code or cypher, preventing unauthorised access. It helps ensure that sensitive information, whether stored or being transferred, is accessible only to those with the correct decryption key. Simply put, encryption is like a lock on a door, and only someone with the correct key can unlock the door.
Encryption and decryption involve mathematical algorithms that follow specific rules or procedures and are often referred to as cryptographic algorithms. Encryption algorithms take plain text (unencrypted data) and convert it into cyphertext (encrypted data). Decryption algorithms then reverse this process, transforming ciphertext back into readable plain text.
These algorithms are based on mathematical principles like modular arithmetic, prime factorisation, and elliptic curve operations. These complex principles make it computationally difficult and almost impossible to reverse the encryption process without the correct key. In video conferencing, encryption helps keep the data, including video, protected and accessible only to the intended recipients.
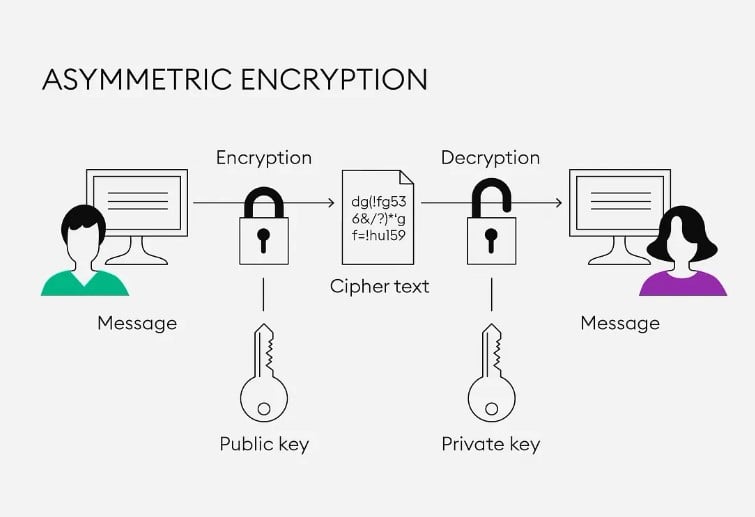
There are two commonly used encryption techniques in organisations around the world: private key cryptography and public key cryptography. In private key cryptography, the same key is used for encryption and decryption. The organisation owns the private key, and the people who work in the organisation use the key to access confidential information. You can think of it as using multiple keys of the same pattern to lock and unlock a door.
Public key cryptography, on the other hand, follows an asymmetric approach. In this system, different keys are used for encryption and decryption, providing an extra layer of security. A public key, available to everyone, encrypts the data. The private key, owned by the intended user, decrypts the data.
Types of Encryption Used in Video Conferencing
As businesses increasingly rely on video conferencing, the security of sensitive data shared during meetings has become a top priority. Encryption is one of the most effective methods to safeguard this data. There are three commonly used encryption types in video conferencing, based on the techniques we just discussed: Data Encryption Standard (DES), Rivest-Shamir-Adleman (RSA), and Advanced Encryption Standard (AES).
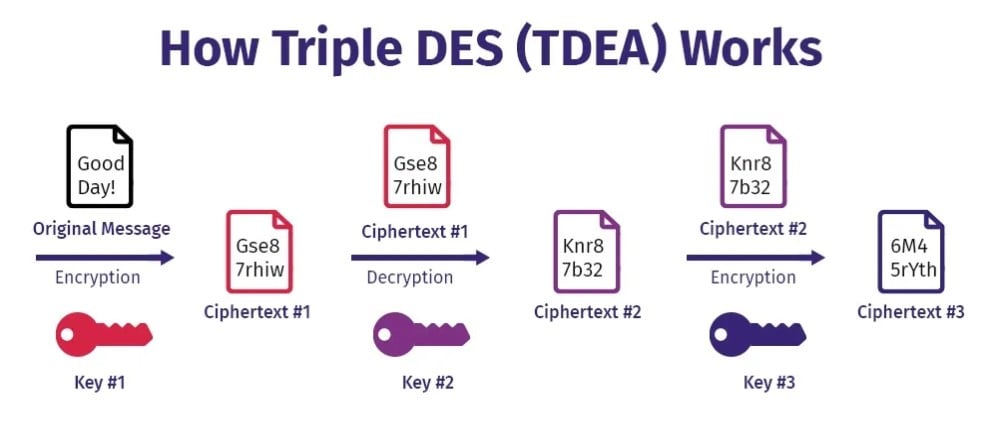
DES was the first encryption standard approved by the U.S. National Institute of Standards and Technology (NIST) in 1977. It was widely used for securing sensitive data in both government and commercial sectors. However, due to its small key size of 56 bits, DES isn’t considered secure anymore. Its successor, 3DES (Triple DES), improves security by using three 56-bit keys, but it comes at a higher computational cost. Even 3DES is slowly being replaced by more modern algorithms.
Similarly, RSA is a widely used public key encryption algorithm designed for secure communication. It uses a public key for encryption and a private key for decryption. It is ideal for securing anonymous transactions and data exchanges. RSA is commonly employed in VPNs and web browsers to authenticate users and ensure data security.
Likewise, AES is the most widely used encryption algorithm nowadays. It encrypts data in blocks rather than individual bits and comes in various versions with different block sizes and encryption rounds (AES-128, AES-192, AES-256). Due to its strength and efficiency, AES is the current industry standard and is used by organisations worldwide, including the US National Security Agency.
Exploring a Use Case of Encryption in Video Conferencing Tools
Let’s consider a situation: you are working as an auditor in a large accounting firm, and you need to discuss confidential financial reports with a client. These reports often contain personal and sensitive information like profit margins, revenue from operations, expenses, and other internal financial strategies, and need to be protected at all times. You’ve decided it’s best to have a meeting over a secure video conferencing platform that has advanced encryption standards to prevent unauthorised access.
When you initiate the meeting, your caller ID and the client’s caller ID will be authenticated using multi-factor authentication in the background. Once verified, the call will begin. Now, end-to-end encryption (E2EE) will be activated. In E2EE, the video, audio, and the files shared are encrypted on your device and decrypted only on the client’s device. It prevents anyone, including the video conference service provider, from accessing the data shared in the call.

During the meeting, you share multiple reports through the platform. To protect the data during transmission, the platform uses Transport Layer Security (TLS). The TLS will encrypt the data and ensure that even if the data were intercepted in transit, it would remain unreadable.
Also, only you and the client have the necessary permissions to view or download the documents, so the access is controlled. If the meeting is being recorded for compliance reasons, the recording is encrypted and securely stored, accessible only to authorised personnel. The scenario we just walked through shows how secure communication can flow while sensitive details remain confidential. You can confidently discuss important matters without the risk of data breaches or leaks.
The Future of Encryption in Video Conferencing
As cyber threats become more sophisticated, encryption technologies are also evolving to protect sensitive data. We are starting to see new methods like homomorphic encryption and quantum cryptography helping with this. Homomorphic encryption lets you process encrypted data without having to decrypt it. Meanwhile, quantum cryptography uses principles of quantum mechanics to share encryption keys securely. It is close to impossible for attackers to intercept it without being detected. These advancements are making encryption more flexible and capable of responding to increasingly complex attacks. They provide greater protection in the face of growing threats.
At the same time, end-to-end encryption is becoming the gold standard for secure video calls. End-to-end encryption boosts security by locking out the service provider so that only the people directly involved in the conversation can access the related data. As more companies and individuals prioritise security, we’ll likely see end-to-end encryption become the default for video conferencing platforms. It’s a shift in secure video conferencing that will offer peace of mind and help keep sensitive discussions to remain private and secure in a world where online communication is the norm.
A Final Look at Encryption and Secure Video Conferencing
Video conferencing is a big part of how we connect today, especially at work. But with this convenience comes the risk of sensitive information being exposed to hackers. Encryption plays a key role in protecting these calls by keeping all shared data secure. It works like a lock that makes it secure so that only the right people can access information. As cyber threats get smarter, new methods like homomorphic encryption and quantum cryptography are being developed to make video calls even more secure. End-to-end encryption is now becoming the standard to ensure that no one except the intended participants can access the conversation. In the future, secure video conferencing will be crucial for keeping online interactions safe from breaches.
Continue reading: Are Offices the Same in the Era of Remote Collaboration?
Sources for the Images
-
Chukwuemeka-Awuja, N. (2024) ‘Asymmetric and Symmetric Encryption For Beginners— Part 1’, Medium, 13 January.
-
InfosecTrain (2023) ‘What is a Man-in-the-Middle (MITM) Attack?’, InfosecTrain, 16 June.
-
Nagaraj, K. (2023) ‘Triple DES (3DES) Encryption — Features, Process, Advantages, and Applications’, Medium, 28 February.
-
Precedence Research (2024) Video Conferencing Market Size, Share, and Trends 2024 to 2034.
-
Suriya (2022) ‘Cryptography Algorithms that a dev must know’, Medium, 4 November.
-
Thananit_s (2024) ‘Rear view of Asian woman working and online meeting via video conference with colleague’, Envato Elements.
References:
-
Bradley, T. (2020) ‘You shouldn’t sacrifice security to video conference during Coronavirus quarantine’, Forbes, 23 April.
-
Brilliance (2024) What Is the Future of Encryption in Cybersecurity?.
-
Jones, C. (2024) ‘German defense chat overheard by Russian eavesdroppers on Cisco’s WebEx’, The Register, 4 March.
-
McAfee (2020) New McAfee Report Estimates Global Cybercrime Losses to Exceed $1 Trillion.
-
Precedence Research (2024) Video Conferencing Market Size, Share, and Trends 2024 to 2034.
-
Tudor, C. (2022) ‘The Impact of the COVID-19 Pandemic on the Global Web and Video Conferencing SaaS Market’, MDPI Electronics Journal, August.
